Most information technology (IT) security professionals are familiar with ISO/IEC 27001, but many that I speak with don’t really know how to approach their operational technology (OT) environments. I often get the question: “Doesn’t ISO/IEC 27001 work for both our corporate and security needs?” The answer is yes and no. ISO/IEC 27001 is a global framework used for information security programs and defines a wide range of requirements as well as guidance for those implementing best practices. The standard has been around for 20 years and went through a major overhaul in 2022. The new version is often referred to as ISO/IEC 27001:2022 and the previous version ISO/IEC 27001:2013.
Anyone who is certified in ISO/IEC 27001 will be required to follow the 2022 version in 2025, so many of us are saying goodbye to 2013. The ISO/IEC 27001 framework has everything from controls around background checks to policies around what is acceptable, and includes technical topics such as vulnerability management. The great thing about ISO/IEC 27001 is that it can be audited by a third party and your organization can be certified in the framework.
Are industrial systems covered by ISO/IEC 27001?
Many of the controls in ISO/IEC 27001 also apply to industrial security; however, they will need to be adapted within industrial environments. There are also gaps in ISO/IEC 27001 that do not deal with areas that are critical to industrial security. This is where ISA/IEC 62443 2-1 comes into play. This international standard has been developed by the International Society of Automation (ISA) which will “cohabitate” within your ISO/IEC 27001 program. For ISO/IEC 27001 organizations, think of ISA/IEC 62443 2-1 as an extra set of tools that will help you defend against threats to your OT environment.
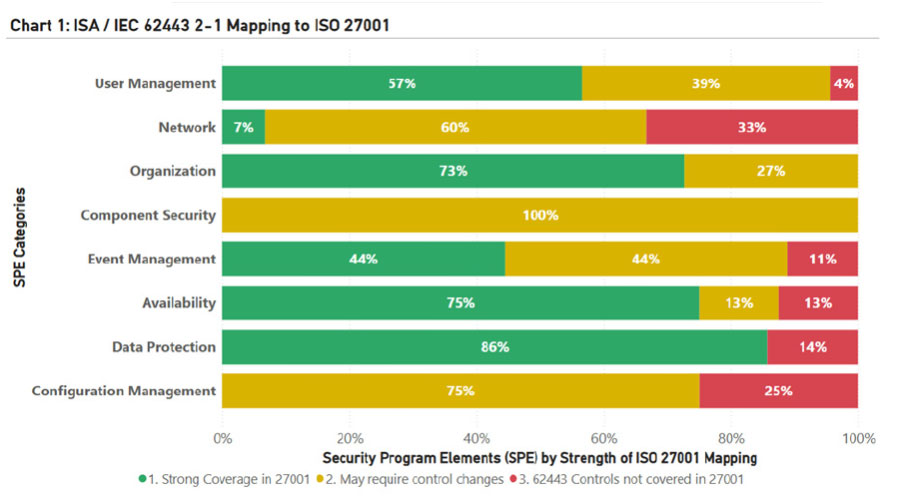
Although there are other standards in the ISA/IEC 62443 framework, I will start with 2-1 because it identifies the key program elements much like the Information Security Management System (ISMS) does in ISO/IEC 27001. In ISA/IEC 62243, the requirements are grouped in security program elements (SPEs) that align with what ISO/IEC 27001 would refer to as controls. With ISA/IEC 62443 2-1, 87 different requirements are grouped into eight SPEs. In Chart 1, I have mapped each of these SPE categories into the respective ISO/IEC 27001: 2022 controls and categorized these by how well the two frameworks map. I have done this mapping based on my own judgment and experience with the frameworks, and this chart should be used for directional guidance only.
To summarize, the mapping falls into three categories:
- Strong coverage in ISO/IEC 27001: For these controls, I felt that most of the ISO/IEC 27001 controls would meet ISA/IEC 62443 2-1 requirements without any changes.
- May require control changes: For these controls, I have highlighted the areas that may require changes to the program.
- ISA/IEC 62443 controls not covered in ISO/IEC 27001: These controls are not included in ISO/IES 27001 because they are unique to industrial systems.
These include items such as security policies, hiring processes, executive engagement, etc.
A note of caution: This does assume that you have ISO/IEC 27001 controls applied at an enterprise level and that your industrial operations follow the same standard.
For example, I assume that you do background checks and security policies for all employees, including corporate and production.
Many of these controls may require a change to your ISO/IEC 27001 control to account for differences with OT environments.
I will discuss this in a little bit, but these include things like plant safety, OT segmentation and some of the unique remote access challenges that OT systems must deal with.
What is missing in ISO/IEC 27001 that is in ISA/IEC 62443 2-1?
Generally speaking, four main areas are unique to industrial security and are not included in ISO/IEC 27001. I will briefly highlight these now, but will be digging into each of these in a future article. OT security network architecture. There are best practices for how you segment and protect different layers of an OT network. The ISA/IEC 62443 standards introduce the concept of zones and conduits to put layers of defense around critical systems.
Think of zones as firewalled security segments and conduits as the communications that flow between those segments. If you have multiple locations and control systems in your environment, it usually makes sense to start with the zones that are connected to the Internet or the corporate network and go from there. The ISA/IEC 62443 standards also detail specific requirements for wireless networks. Safety systems security. Most IT systems don’t have to deal with the safety of people or the environment, but as you would expect, safety is the number one priority in industrial environments.
Safety systems are independent of the systems that control production and are there to ensure that the line does not do something that could cause harm. A safety system may, for example, monitor the temperature of an oven and if it heats up above safe temperatures, then it will take independent actions to cool it. The challenge with safety systems is that these have traditionally been designed to avoid kinetic events, and most engineers have not considered the “cyber threat” into their design. Companies may, for example, have safety systems on the same networks as control systems and a cyberattack would likely impact both of them.
Operational independence. OT systems must be able to run independently during a cyber event and must always be safe. With increases in ransomware over the past few years, it is important that every organization understands the impact of these events on its production facilities. In some cases, completely disconnecting the OT network from corporate or Internet communication may be required, and organizations should understand the process to do this and the conditions under which they would make this decision.
Remote access. ISO/IEC 27001 does have controls related to remote access to corporate assets. However, industrial systems have unique requirements that should be further understood. OT environments often have third-party maintenance and support suppliers that must access critical networks and these need to be done both efficiently and securely.
Can I implement all of my ISO/IEC 27001 controls in my OT environment?
Not all ISO/IEC 27001 controls will work in OT environments in the same way that they do in corporate environments and can, in fact, create big issues. Here are a few notable controls that will need to be adapted for OT.
- Vulnerability management and patching. In many cases, vulnerability programs may not be implemented for OT systems and these will likely require a different approach than what is used in the corporate environments.
- Clear desk and clear screen. In OT environments, it is important not to lock operator screens that are needed in an emergency.
- Malware protection. Any anti-malware or endpoint detection and response (EDR) tool should be tested thoroughly, as these can cause major issues on OT systems.
- Backup systems. Contrary to what many engineers will tell you, OT systems can and should be backed up.
Many vulnerability scanning systems that work on a corporate environment could cause issues in industrial environments, and so different processes and/or tools may be required.
Organizations should, however, implement mitigating controls such as physical security, monitoring or limitations of access to lower the risk.
Many OT suppliers test specific anti-malware applications on their environments.
The suppliers may specify certain EDR suppliers and specific configuration settings for these environments.
Often, there are specialized approaches to these backups.
Immutable backup solutions that prevent an attacker from deleting backups should be implemented to avoid catastrophic results.
Wrapping up
Hopefully, this article has pointed you in the right direction if you are building your industrial security program. In future articles, I will outline steps that can get you started on implementing ISA/IEC 62443-2-1, and will dig a little deeper into some of the controls that are unique to the framework from ISO/IEC 27001. Further resources are also available from the International Society of Automation Global Cybersecurity Alliance ( ISAGCA ):
- Applying ISO/IEC 27001/2 and the ISA/IEC 62443 Series for Operational Tech Environments
- Understanding the ISA/IEC 62443 Series of Standards from an ISO/IEC 27001 and ISO/IEC 27002 Perspective.
This feature also appears in Automation.com Monthly's 2nd Annual Cybersecurity Trends report (October 2025).
